It Could be You: Preventing Doxxing, Hacking, and Spying
National Young Feminist Leadership Conference 2017
Beth Soderberg
Digital Programs Director, Feminist Majority Foundation
@bethsoderberg
webmaster@feminist.org
Photo by Alvimann on Morguefile
Photo by geralt at pixabay.com
It Could Be You
Doxxing
Doxing (from dox, abbreviation of documents), or doxxing, is the Internet-based practice of researching and broadcasting private or identifiable information (especially personally identifiable information) about an individual or organization.
- name
- address
- birthday
- social security number
- phone numbers
- financial information
- relationship information
- private photos
- private videos
- harassment
- bullying
- cyber and physical stalking
- physical threats
- identity theft
- extortion
Step 1: Remove Your Personal Information from the Internet
Step 1: Remove Your Personal Information from the Internet
opt out of data brokers
...quarterly
Step 1: Remove Your Personal Information from the Internet
don't publish your information
Step 2: Pay for Private Domain Registration
Step 2: Pay for Private Domain Registration
you won't be findable on WHOIS
WHOIS documents who is responsible for a domain name's registration.
- name
- address
- phone number
- administrative contacts
- technical contacts
Step 3: Check Social Media Privacy Settings
Step 3: Check Social Media Privacy Settings
assume there is no privacy
Step 3: Check Social Media Privacy Settings
remove anything you've said that is embarrassing
Step 4: Google Yourself
Step 4: Google Yourself
log out of everything and be incognito
Step 4: Google Yourself
set up a simple website with a name-oriented domain name
Step 4: Google Yourself
optimize your online presence
If You Are Doxxed
If You Are Doxxed
stay calm: the goal is for you to overreact
If You Are Doxxed
take screenshots of everything
If You Are Doxxed
report threats of violence to the police & FBI
If You Are Doxxed
file complaints with Twitter, Reddit, etc.
If You Are Doxxed
change all of your passwords
If You Are Doxxed
consider changing your phone number
If You Are Doxxed
take care of yourself
Hacking
to circumvent security and break into (a network, computer, file, etc.), usually with malicious intent
Our Goal Here: Stop 99% of Attacks
Step 1: Use Unique Passwords
Step 1: Use Unique Passwords
passwords should be:
- difficult for someone else to guess
- easy for you to remember
- not reused across multiple accounts
Step 1: Use Unique Passwords
passwords should not be:
- birthdays (of you or people close to you)
- “password” or “secret” or “qwerty”
- the same word repeated over and over
- names of pets or children
- anything someone could guess from your social profiles
Step 1: Use Unique Passwords
the most secure passwords are very long and easy to remember
Step 1: Use Unique Passwords
don't send passwords over email, text, instant message
Step 1: Use Unique Passwords
use a password manager
Step 2: Use Two-Factor Authentication
Step 2: Use Two-Factor Authentication
Multi-factor authentication (MFA) is a method of computer access control in which a user is granted access only after successfully presenting several separate pieces of evidence to an authentication mechanism – typically at least two of the following categories: knowledge (something they know), possession (something they have), and inherence (something they are).
Two-factor authentication...is a method of confirming a user's claimed identity by utilizing a combination of two different components.
Step 2: Use Two-Factor Authentication
even if someone has your password, they won't be able to get in
Step 2: Use Two-Factor Authentication
places to set this up
Step 3: Lock Down Your Privacy Settings
Step 3: Lock Down Your Privacy Settings
questions to ask
- Is your location publicly viewable?
- Is your birthday publicly available?
- Can people learn your habits?
- Can people figure out the answers to your security questions through what you post?
Step 4: Lock Down Your Email
Step 4: Lock Down Your Email
your email is your MOST important account
Step 4: Lock Down Your Email
run Google's Security Checkup
Step 4: Lock Down Your Email
recognize and avoid fraudulent emails
- no one legitimate will ever ask you for your password
- don't believe anyone "from IT" who calls to help you "fix" your account
Step 4: Lock Down Your Email
scam emails
- “Nigerian Prince” scam
- Sudden inheritances from long-lost relatives
- Relative traveling abroad, got hurt, needs help
- Fake US government emails targeting immigrants
- These scams almost always revolve around money
- If it’s too good to be true, it probably is
Step 4: Lock Down Your Email
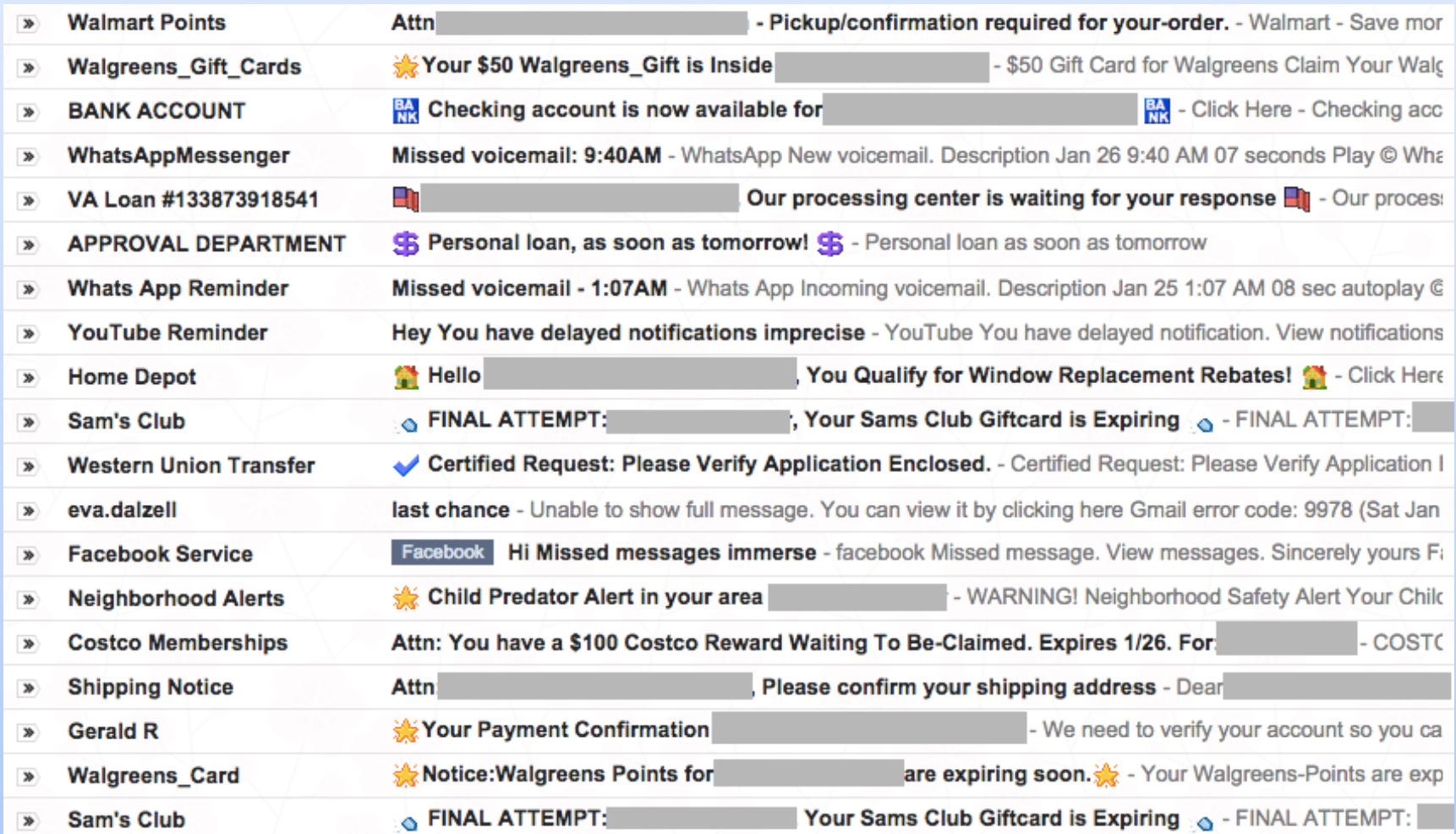
Step 4: Lock Down Your Email
if you're not sure, log into your actual account for whatever it is
Step 4: Lock Down Your Email
verify the sender
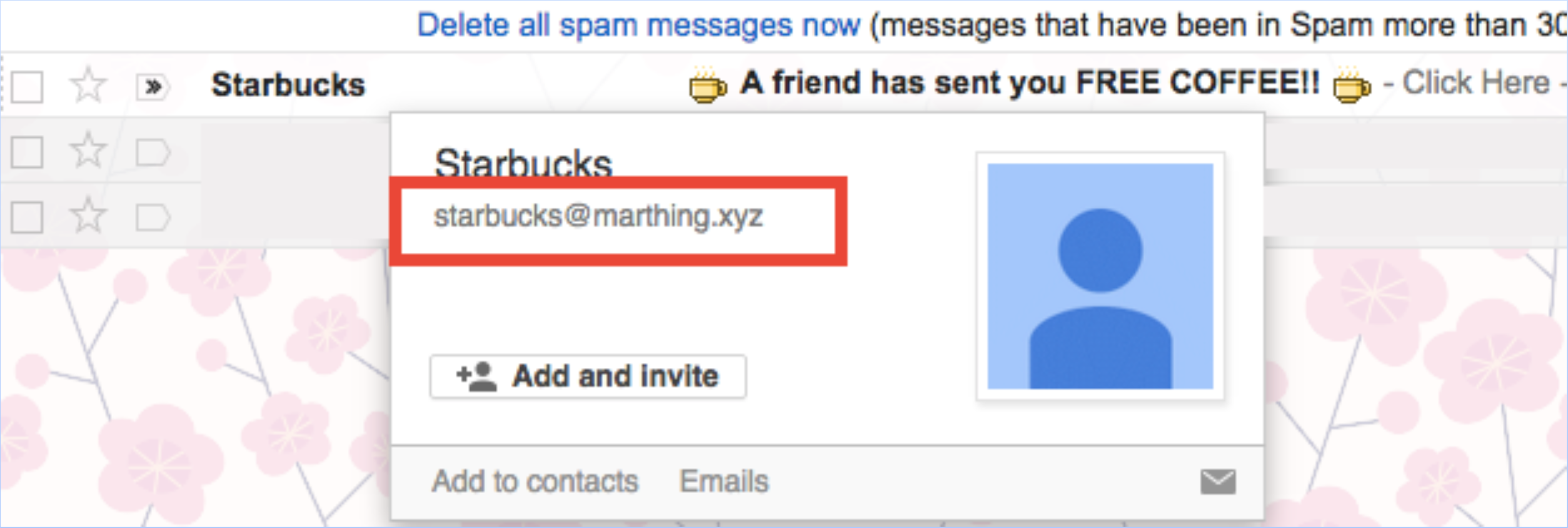
Step 4: Lock Down Your Email
verify links
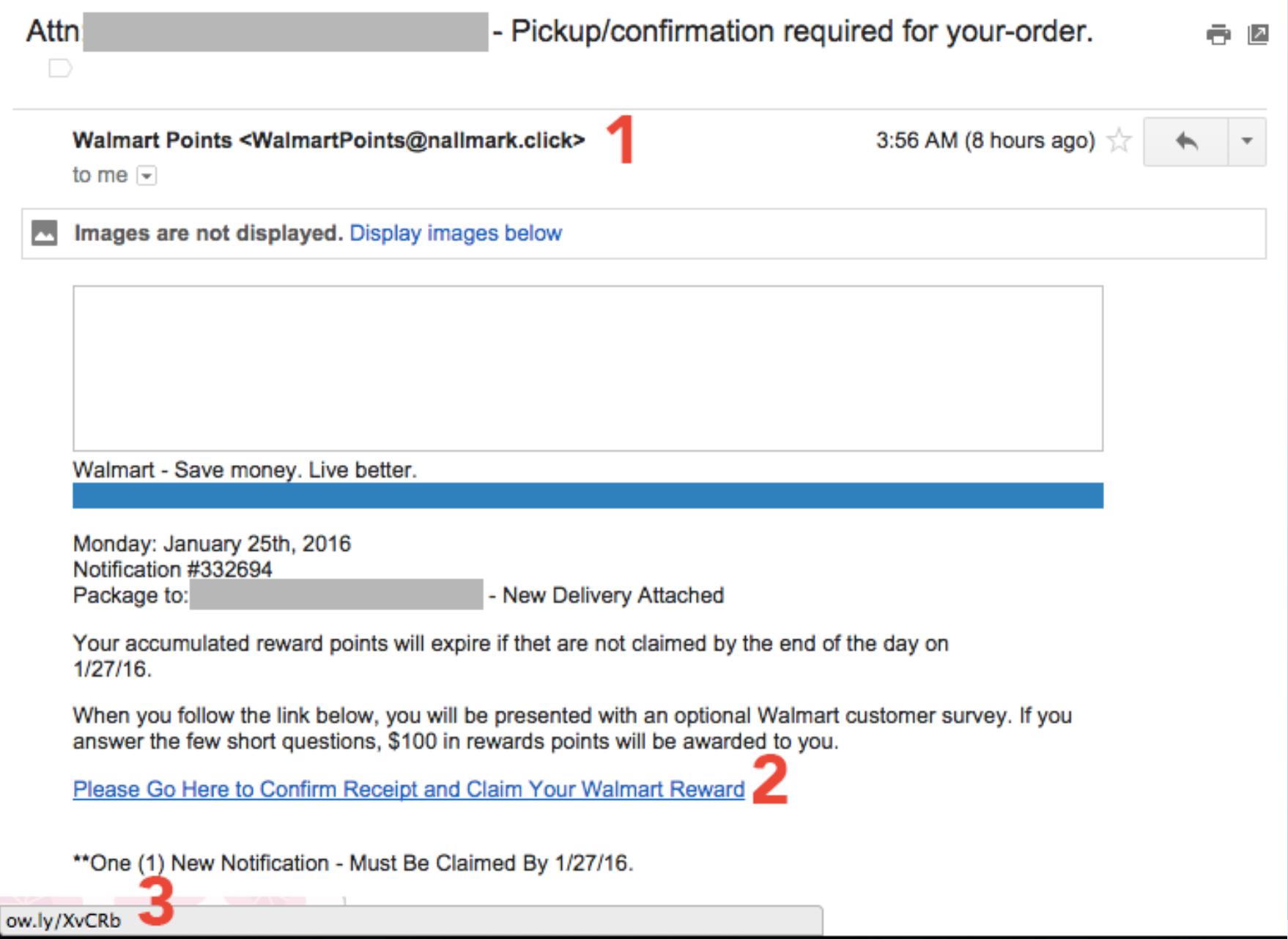
Step 4: Lock Down Your Email
never open attachments you're not expecting
- be careful with emails you weren’t expecting telling you to open a link or download an attachment
- frequently they will appear to come from friends or colleagues
- they’ll commonly have little or no explanation other than “click here” or “download this”
Step 4: Lock Down Your Email
some attachments aren't actually attachments
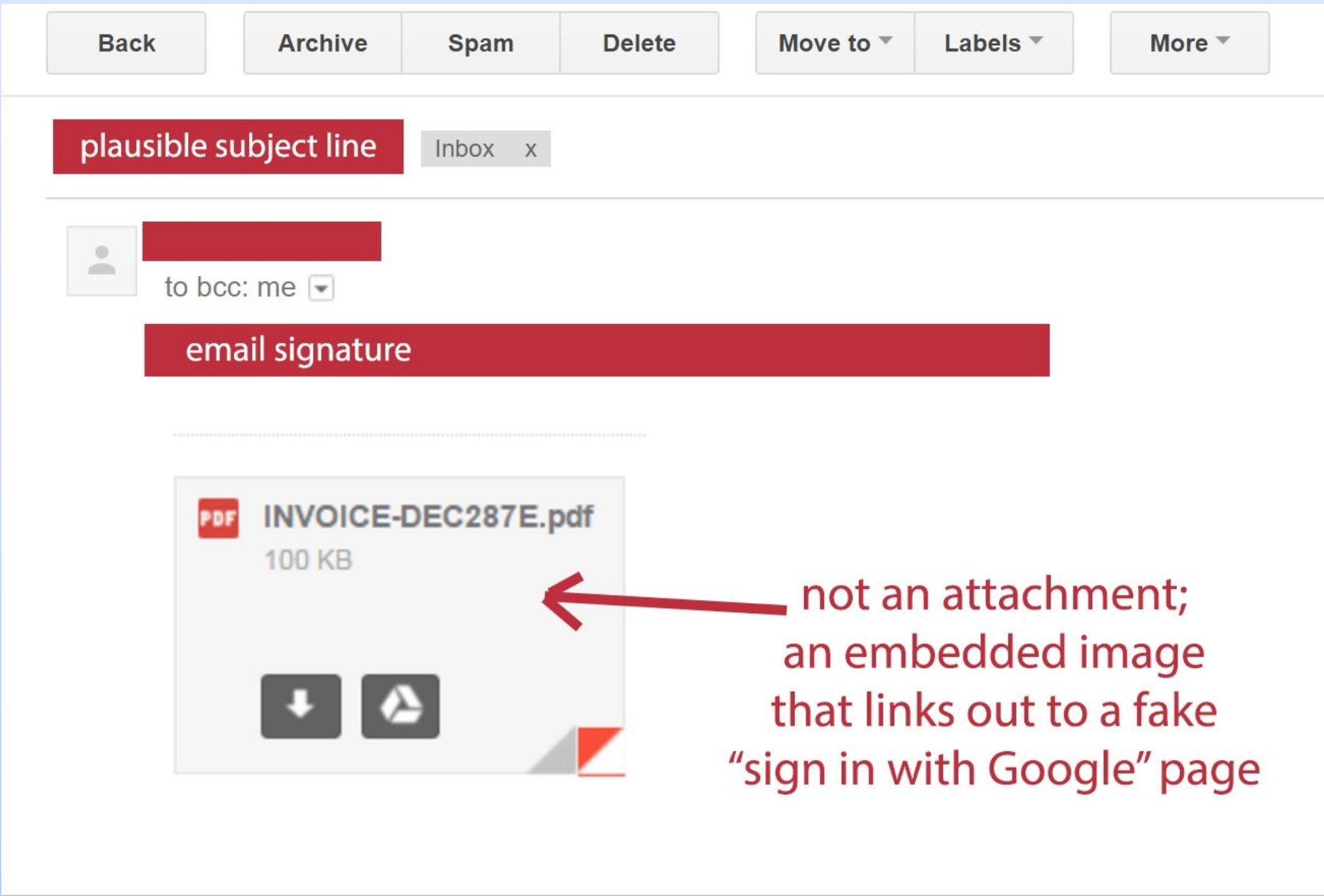
Step 4: Lock Down Your Email
questions to ask about suspicious emails
- Were you expecting the email?
- Is it from someone you know?
- Can you verify they sent it?
- Check the reply-to address.Was it actually from them?
- Is it possible their email address is compromised?
- Is it from someone you haven’t heard from in a long time?
Step 4: Lock Down Your Email
if you think an email is fraudulent, delete it!
Step 4: Lock Down Your Email
heads up for suspicious texts too
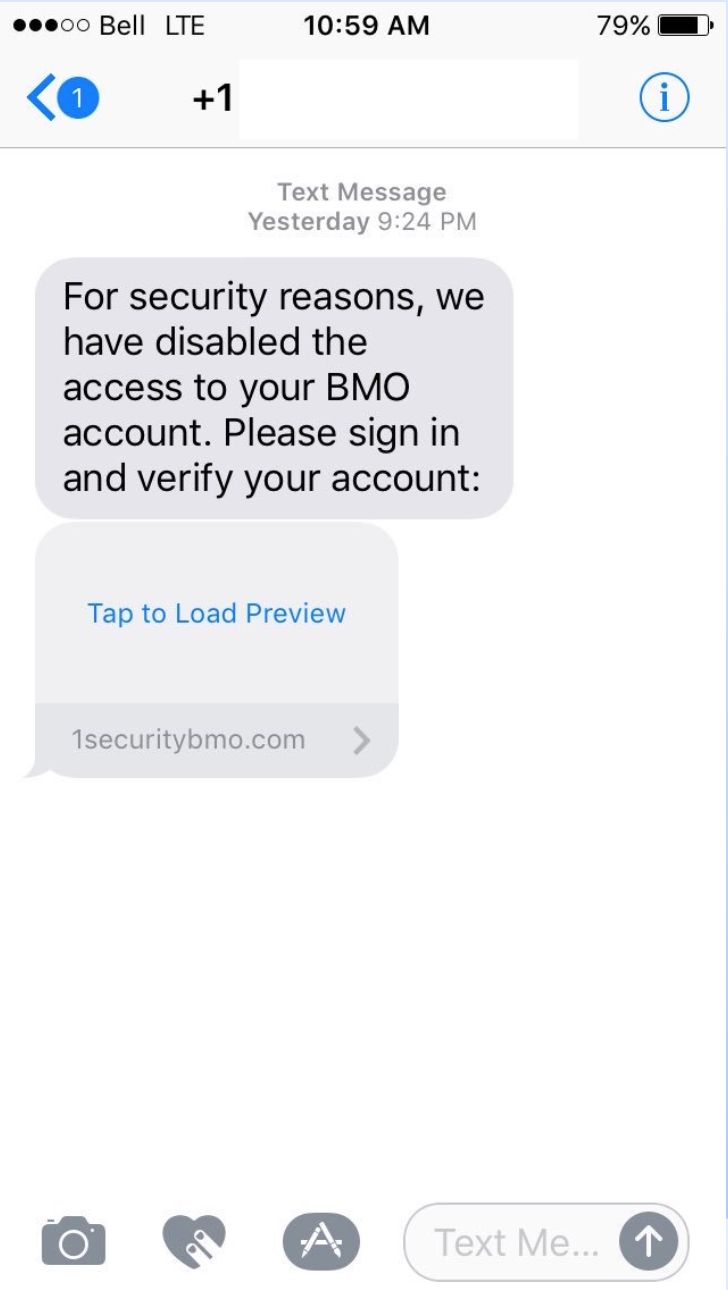
Step 4: Lock Down Your Email
what would you do with this?
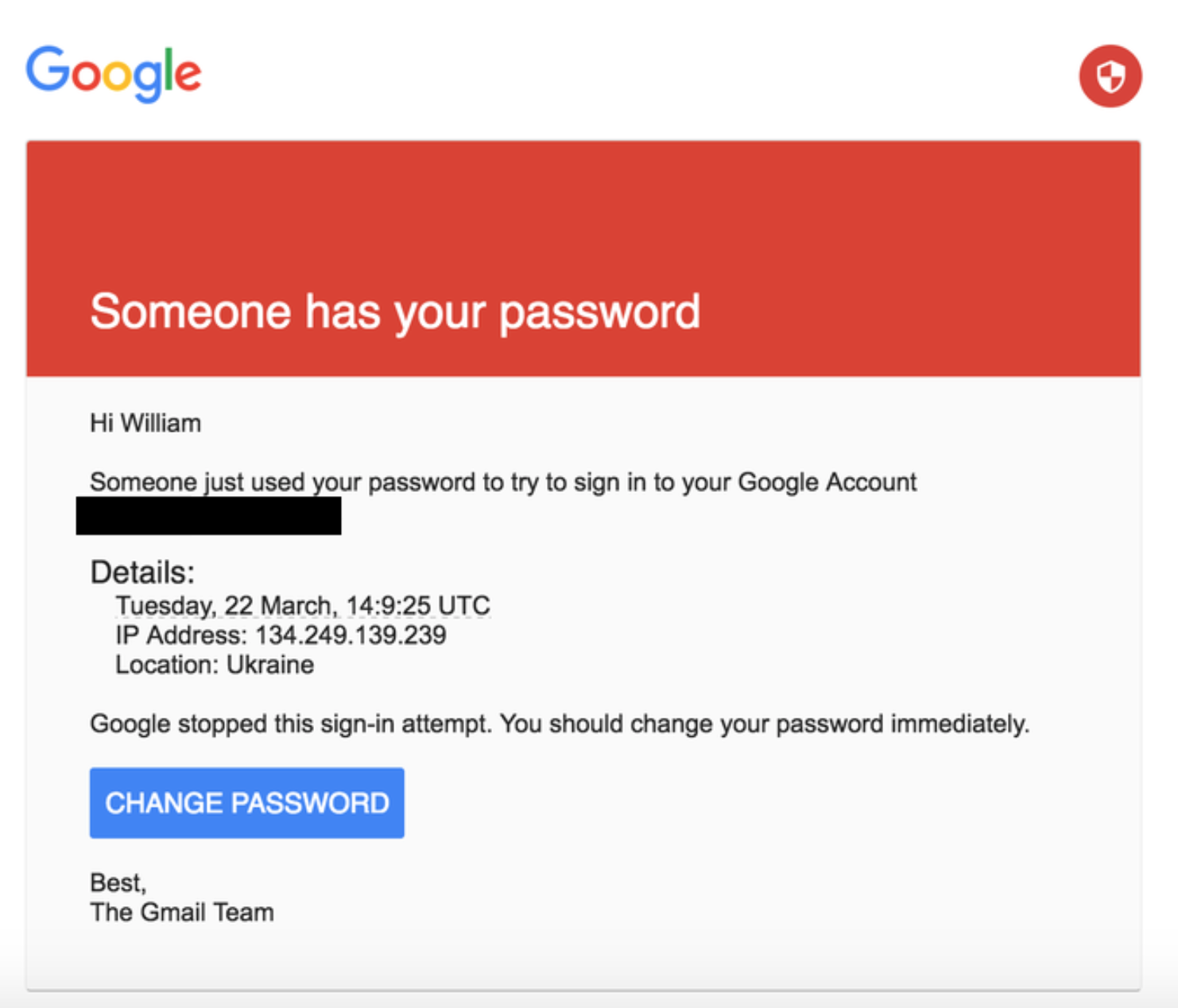
Step 4: Lock Down Your Email
if you clicked, you'd get...
Step 5: Lock Down Your Important Accounts
Step 5: Lock Down Your Important Accounts
make a list
- online banking, loans, anything financial
- anywhere you’ve saved a credit card (Amazon, etc.)
- social media
- what else?
- use this sample worksheet
Step 5: Lock Down Your Important Accounts
for each account
- use strong passwords
- use two-factor authentication
- review your security and privacy settings
Step 6: Lock Down Your Computer
Step 6: Lock Down Your Computer
run available updates
Step 6: Lock Down Your Computer
back up everything
Step 6: Lock Down Your Computer
store a backup somewhere where you don't live
Step 6: Lock Down Your Computer
enable passwords for your computer
Make sure you need to enter a password to access your computer:- on startup
- on waking up from sleep
- on exiting the screensaver
Step 6: Lock Down Your Computer
lock your computer when you leave it
- on Windows, the keyboard shortcut to lock your computer is Windows + L
- on a Mac, you can set up your Hot Corners to lock your screen
Step 6: Lock Down Your Computer
lock your phone: it's a mini computer
- iPhone users, make sure your password is at least 6 digits long
- Android users, use a long, complicated pattern to unlock
- Police can force you to unlock your phone with your fingerprint, but can’t ask for your password
Step 7: Use the Internet Carefully
Step 7: Use the Internet Carefully
fake websites look real
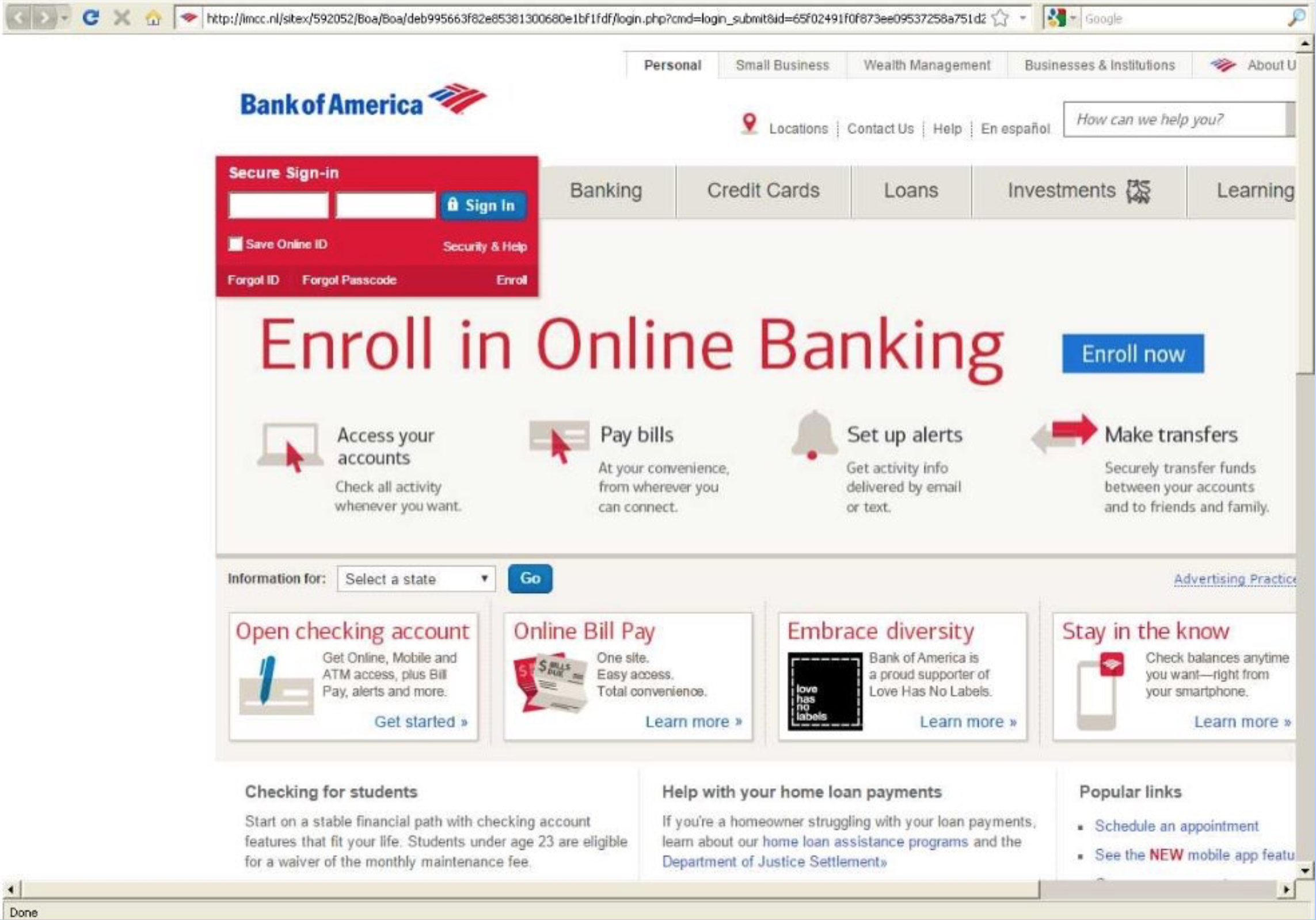
Step 7: Use the Internet Carefully
verify URLs
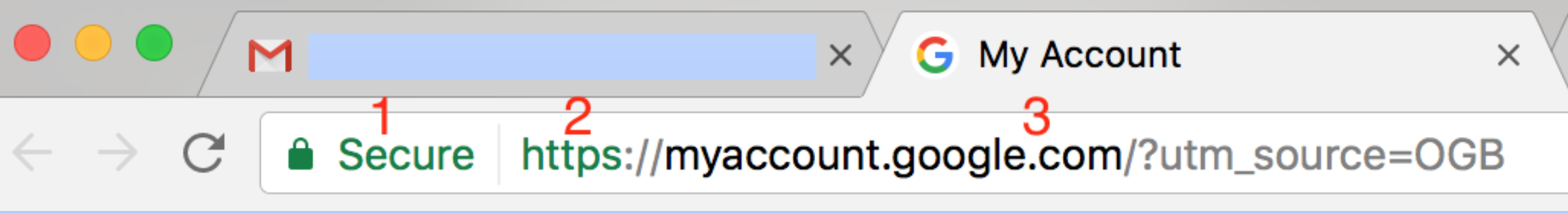
Step 7: Use the Internet Carefully
fraudulent URL examples
- https://mygoogleacount.com/securityAlert
- https://bankofarnerica.com/sign-in/index.php
- https://onlinebanking.wellsfargo.wells-fargo-online- banking.com/myaccount.aspx
- https://twitter.com.twitter-followers.link/unfollowers
- https://myaccount.google.com/?utm_source=OGB
Step 7: Use the Internet Carefully
be careful what you download
- Don’t download counterfeit software
- Don’t download programs that promise free system scans or PC speed boosts
- Download software only from trusted websites
Spying
- One who secretly collects information concerning the enemies of a government or group.
- One who secretly collects information for a business about one or more of its competitors.
- One who secretly keeps watch on another or others.
Spying
anything you have stored on someone else's servers is at risk
- browsing data and history
- emails
- chats
- videos
- photos
- file transfers
- social media interactions
Spying
courts can subpeona private companies to hand over your data
Step 1: Hide Your Browsing Data
Step 1: Hide Your Browsing Data
your browsing data is:
- sites you go to
- links you click on
- ads you see
- where you hover
Step 1: Hide Your Browsing Data
use a vpn
A virtual private network (VPN) is a virtualized extension of a private network across a public network, such as the Internet. It enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
Step 1: Hide Your Browsing Data
here's an article to learn how to set up a VPN for your computer or phone
Step 1: Hide Your Browsing Data
beware of public wifi
Step 2: Try to Fortify Your Email Account
Step 2: Try to Fortify Your Email Account
email is inherently insecure
Step 2: Try to Fortify Your Email Account
heads up: gmail scans your messages
Step 2: Try to Fortify Your Email Account
check out Pretty Good Privacy
Step 3: Encrypt Your Chats, IMs, Texts
Step 3: Encrypt Your Chats, IMs, Texts
off the record (OTR) messaging
Both people need to enable OTR messaging on the chat client.
Adium and Pidgin provide OTR encryption capabilities for:
- Google Talk
- Facebook chat
- AIM
- some others
Step 3: Encrypt Your Chats, IMs, Texts
check out Cryptocat
Step 3: Encrypt Your Chats, IMs, Texts
check out SafeChats
Step 3: Encrypt Your Chats, IMs, Texts
look for messaging apps with end to end encryption
- Telegram
- Silent Text
- Threema
Step 3: Encrypt Your Chats, IMs, Texts
use Signal for texting
Step 4: Be Aware of Metadata on Your Phone
Step 4: Be Aware of Metadata on Your Phone
metadata includes
- who you call/who calls you
- length of calls
- location data/geotracking
- browsing data
- app usage
Step 5: Know Your Social Network Can (Easily) Be Mapped Whether You Participate Online or Not
Step 5: Know Your Social Network Can (Easily) Be Mapped Whether You Participate Online or Not
Play with Immersion from MIT's Media Lab
tl/dr: everything you do online could be public, be careful!
Thank you!
* Special thanks to Shannon Turner of Hear Me Code for her open source Security is for Everyone training. Parts of this workshop derive from this training.